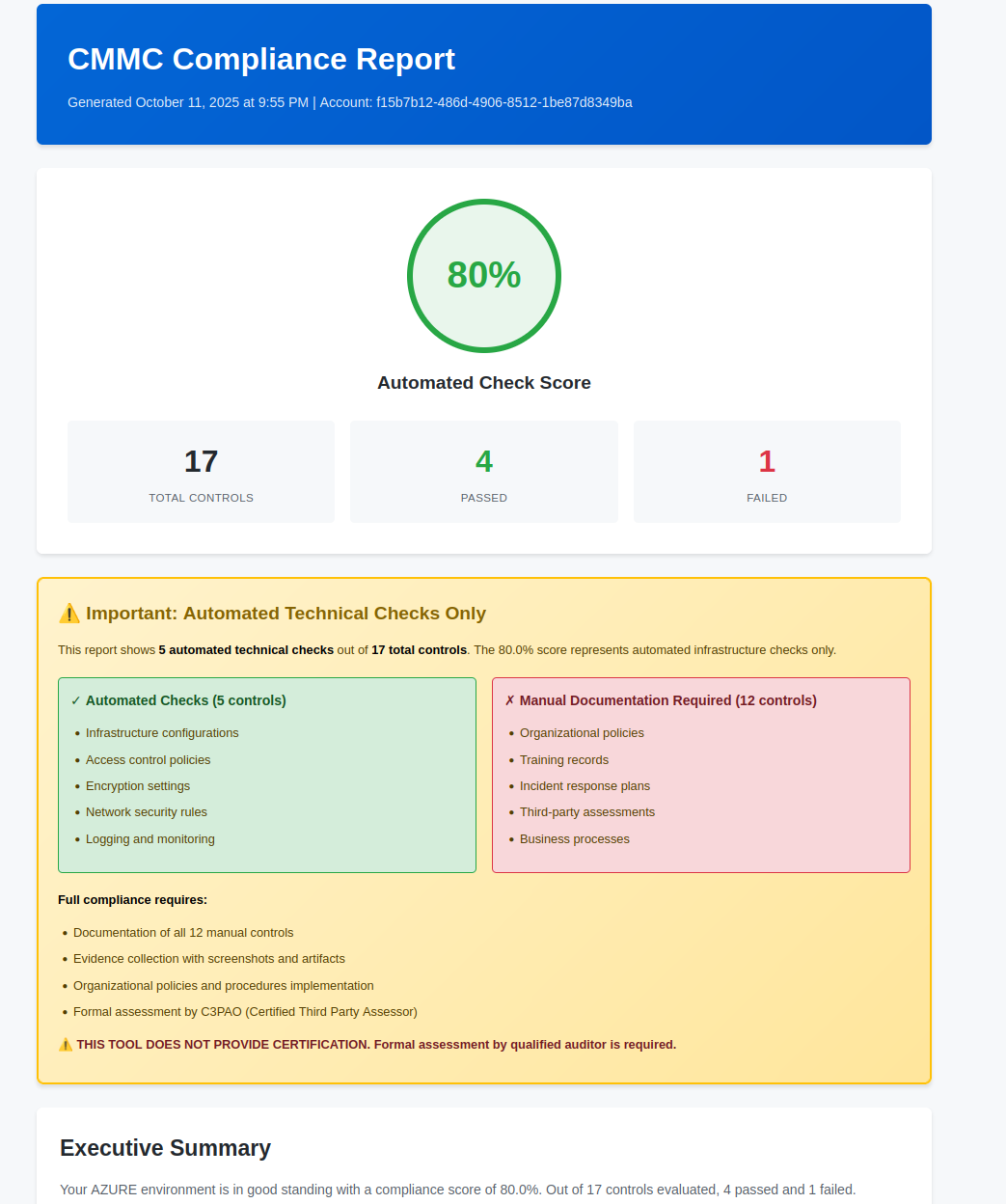
See It In Action
Real scan outputs and reports from actual customer environments
What a PASS Looks Like
Controls that meet compliance requirements show specific evidence of what's configured correctly.
✓ PASS | CC6.3 - Encryption at Rest All 15 S3 buckets have encryption enabled → Meets SOC2 CC6.3, PCI DSS 3.4, HIPAA 164.312(a)(2)(iv)
What a FAIL Looks Like
Failed controls show exactly what's wrong, how to fix it, and what evidence you'll need for auditors.
Fix: aws ec2 revoke-security-group-ingress \ --group-id sg-0ab56571076bcff37 \ --protocol tcp --port 22 --cidr 0.0.0.0/0
Evidence needed: 1. Go to EC2 → Security Groups 2. Screenshot 'Inbound rules' tab 3. Show NO rules with 0.0.0.0/0 for port 22
Want to see more examples?
Browse terminal scan outputs, PDF reports, console screenshots, and more evidence samples.
Browse All Examples →